Abstract: The information security mechanism of Bluetooth is analyzed in detail, and the algorithms and implementation steps of each part are discussed in detail. And made a certain assessment of the security of the existing Bluetooth specification, according to its shortcomings proposed a new security mechanism built by the DES algorithm, which can meet the high security requirements of Bluetooth applications.
As an emerging short-range wireless communication technology, Bluetooth has been widely used in various fields. It provides low-cost, low-power, short-range wireless communication, forming a personal network in the communication environment of fixed and mobile devices, making Various information devices can achieve seamless resource sharing.
Since the Bluetooth communication standard uses radio waves as a medium, third parties may easily intercept information, so Bluetooth technology must adopt certain security protection mechanisms, especially in electronic transaction applications. In order to provide security and credibility of information, the system must provide security measures at the application layer and link layer. 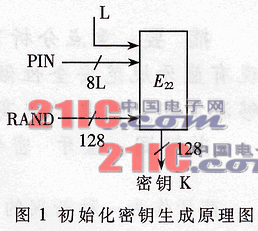
This article focuses on the principles of Bluetooth information security mechanism and related algorithms, and points out its shortcomings and problems in security. Because for most applications that require privacy to be considered first, the data security provided by the current Bluetooth standard is insufficient. The encryption of the 128-bit key length sequence adopted by the current Bluetooth specification can be cracked in some cases. This paper also proposes an improved scheme of Bluetooth security mechanism, that is, the use of DES encryption system to build a strong keying algorithm, which can prove that this encryption algorithm is safe and reliable.
1 Bluetooth security mechanism
The security mechanism adopted by Bluetooth is suitable for peer-to-peer communication, that is, both parties implement the authentication and encryption procedures in the same way. The link layer uses 4 entities to provide security: a public Bluetooth device address with a length of 48 bits; an authentication key with a length of 128 bits; an encryption key with a length of 8 to 128 bits; and a random number with a length of 128 bits. The following focuses on the composition of Bluetooth security mechanisms and related algorithms.
1.1 Random number generator
Random number generators have important applications in the Bluetooth standard, such as in generating authentication keys and encryption keys, and query-response schemes. The ideal method for generating random numbers is to use real random number generators with random physical characteristics, such as thermal noise of some electronic devices, etc., but in practical applications, software-based pseudo-random number generators are usually used. The requirements of the Bluetooth system for random numbers are "random generation" and "non-repeatability". "Randomly generated" means that it is impossible to estimate a random value with a probability significantly greater than zero (for a Bluetooth encryption key with a length of L bits, the probability is greater than 1 / 2L).
At present, among many types of pseudo-random number generators, Linear CongruenTIal Generator is the most widely studied and used. The expression is:
Xn + 1 = αXn + c (modm) n≥0.
Where α and c are constants, and m is the modulus, both positive integers. αXn + c modulo m to get Xn + 1. At the beginning, a seed number X0 is given in some way; then the previous random integer Xn is used to generate the next random integer Xn + 1, thereby generating the integer random number sequence {Xn}.
1.2 Key management
The Bluetooth unit key length cannot be preset by the unit manufacturer and cannot be set by the user. The Bluetooth baseband standard stipulates that the encryption key given by high-level software is not received to prevent the user from fully controlling the key length. 
1.2.1 Key type
The link key is a 128-bit random number, which is a temporary or semi-permanent key shared by two or more parties in communication. The semi-permanent link key can be used in several successive authentication processes between shared link units. The typical application of the temporary key is: In the case of point-to-multipoint communication, the same information needs to be sent to multiple receivers securely. At this time, the main unit key is used to replace the current link key. The Bluetooth standard defines four types of link keys: â‘ joint key KAB; â‘¡ unit key KA; â‘¢ temporary key Kmoster; â‘£ initialization key Kinit. In addition, an encryption key Kc is defined, which is generated by the current link key. For the Bluetooth unit, the unit key KA is generated in unit A, and depends on the unit, and rarely changes. Joint key KAB. Generated by the parties A and B. The temporary key Kmoster is only used in the current session, also known as the master unit key. The initialization key Kinit is the link key used in the Bluetooth initialization process. The key is generated by a random number, a PIN code usually in decimal, and the Bluetooth device address BD_ADDR of the initiating unit. The PIN code can be selected by the user or it can be a fixed number provided with Bluetooth. At present, in most applications, the PIN code is a 4-digit decimal number, which cannot provide high security. The Bluetooth baseband standard requires a PIN code length of 1 to 16 bits, so it is recommended to use a longer PIN code as much as possible to enhance security.
1.2.2 Key generation and initialization
Each pair of Bluetooth units to be authenticated and encrypted must perform an initialization process, which consists of the following parts:
(1) Generate the initialization key Kinit: the link key used temporarily during the initialization process. The key is generated by the E22 algorithm and related parameters, and its generating schematic is shown in Figure 1. The 128-bit initialization key Kinit output by E22 is used for the exchange and distribution of link keys. If the applicant and the verifier have not exchanged the link key, Kinit is used in the authentication process, otherwise it is no longer used. This process must be able to resist certain attacks. For example, the attacker uses a large number of fake Bluetooth addresses BD_ADDR to test a large number of PINs. If the device address is fixed, the waiting interval for each test PIN code should increase exponentially.
(2) Authentication: If no communication has occurred between the two units, the initialization key is used as the link key. Every time the authentication procedure is executed, a new random parameter AU_RANDA is issued. In mutual authentication, the authentication procedure is first executed in one direction, and then the authentication is reversed after success. Successful authentication will get an auxiliary parameter ACO, which is the authentication encryption offset. It will be used to generate encryption keys.
(3) Generating unit key: The unit key is generated when the Bluetooth unit is running for the first time, and is generated according to the E21 algorithm and hardly changes. During initialization, both parties of the communication usually select a key in a unit with a small memory capacity as the link key.
image 3
(4) Generate a joint key: The joint key is a combination of two numbers generated in unit A and unit B, respectively. The generation process is: each unit generates random numbers LK_RANDA and Lk_RANDB, using the E21 algorithm and their respective random numbers, Bluetooth addresses to generate another random number LK_KA and LK_KB, and through other operations after the two units to obtain a joint key. Then start the mutual authentication process to confirm the success of the interaction process. After the joint key exchange is successfully distributed, the original link key will be abandoned.
(5) Generate encryption key: The encryption key Kc is derived from the current link key, the 96-bit "encryption offset number" COF and a 128-bit random number according to the E3 algorithm.
(6) Point-to-multipoint configuration: In fact, the master unit informs several slave units to use a common link key to broadcast encrypted messages. In most applications, this common link key is a temporary key, denoted as Kmoster. After Kmoster is received from the unit, it can be used to replace the original link key. The generation process of Kmoster is as follows: First, a new link key Kmoster is generated from two 128-bit random numbers RAND1 and RAND2: Kmoster = E22 (RAND1, RAND2, 16) . Then send the third random number RANO to the slave unit. The master and slave units calculate the 128-bit scrambling code overlay based on E22, the current link key and RAND, and the master unit bitwise XORs the overlay with the new link key. The result is sent to the slave unit, and then Kmoster is calculated. A new ACO value is calculated in the subsequent authentication process.
1.3 Encryption procedures
The encryption of the payload is realized by the stream cipher algorithm, the stream cipher is synchronized with the payload, and the encryption schematic diagram is shown in FIG. 2. The stream cipher system consists of three parts: performing initialization, generating key stream bits, and performing encryption or decryption. The payload key generator combines the input bit streams in the proper order and shifts them into the four linear feedback shift registers LFSR used by the key stream generator. The second part is the main part. The key stream bits are generated according to the method proposed by Massey and Rueppel. This method has been analyzed and studied to prove that it has high encryption performance, but this method may be subject to related attacks. It will be described in detail later.
1.3.1 Agree on the encryption key length and encryption mode
Bluetooth devices implementing the baseband standard need to define the maximum allowable key byte length Lmax, 1≤Lmax≤16. Before generating the encryption key, the relevant units must agree on the actual length of the key. The master unit sends the recommended value L (M) sug to the slave unit. If L (S) min≤L (M) min and the slave unit supports the recommended value, the slave unit confirms this, and L (M) min becomes the value of the encryption key length for this link. If the above conditions are not met, the slave unit will send a new recommended value L (S) min <L (M) sug to the master unit, and the master unit evaluates this suggestion. Repeat this procedure until an agreement is reached or one party gives up the negotiation.
1.3.2 Encryption algorithm
The encryption procedure uses stream cipher encryption. The encryption system uses linear feedback shift registers (LFSRs). The output of the register system is combined by a finite state machine with 16 states. The output of the state machine is either a key stream sequence or a random initial value during the initialization phase. The encryption algorithm needs to provide the encryption key, 48bit Bluetooth address, clock bit of the main unit and 128bit random number RAND. The principle of the encryption algorithm is shown in Figure 3.
Among them, there are 4 LFSRs (LFSR1, ..., LFSR4), the bit lengths are L1 = 25, L2 = 31, L3 = 33, L4 = 39, feedback polynomial (tap polynomial, characteristic polynomial). The sum of the length of the four registers is 128bit.
These polynomials are primitive polynomials, and the Hamming weight is 5, which can take into account the requirements of the generated sequence with good statistical characteristics and reducing the number of XOR gates required for hardware implementation.
Let xit indicate that LFSRit outputs status bits at all times, and Yt from the quadruple (x1t, ..., x4t) is:
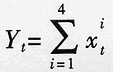 , Where Yt is an integer, and the value is 0, 1, 2, 3, or 4. The addition generator output is given by the following equation:
, Where Yt is an integer, and the value is 0, 1, 2, 3, or 4. The addition generator output is given by the following equation:
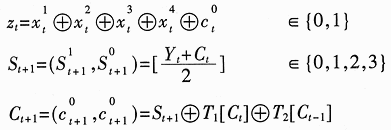
In the formula, T1 [.] And T2 [.] Are two different linear bijections on GF (4).
Before the keystream generator works, it is necessary to load initial values ​​for 4 LFSRs (128bits in total) and determine the C0 and C-14bit values. These 132bit initial values ​​are derived from the specified input volume using the keystream generator. Key Kc, 48bit Bluetooth address and 26bit main unit clock CLK26-1. Encryption algorithm initialization process: (1) Generate an effective encryption key from the 128-bit encryption key Kc, denoted as K'c, let L (1≤L≤16) be the effective key length expressed by the number of 8-bit groups, then K ' c (x) = g2 (L) (x) (Kc (x) modg1 (L) (x)). (2) Move K'c, Bluetooth address, clock and 6bit constant 111001 into LFSR. After the encryption algorithm is initialized, the key stream is output from the addition combiner for encryption / decryption.
1.3.2 Certification
The Bluetooth technology authentication entity uses a so-called check-response scheme. Through the "two-step" protocol, does the applicant know that the secret key is verified using a symmetric key. This means that a correct applicant / verifier pair will share the same key Kc in the verification-response scheme. The verifier will verify whether the applicant can authenticate the algorithm K1 to authenticate the random number AU_RANDA and return the authentication result SERS for inspection . The authentication and encryption key generation function can refer to related materials, omitted here. ?
2 Scheme improvement of Bluetooth security mechanism
There are two main problems with the existing Bluetooth security mechanism. One is the use of the unit key: during the authentication and encryption process, since the unit key has not changed, third parties use this key to steal information. The 128-bit key length E0 sequence encryption can be cracked in some cases by less complicated methods. The other is the insecurity of the personal identification code (PIN code) provided by the Bluetooth unit: since the PIN code is composed of 4 decimal digits in most applications, it is easy to attack successfully using the exhaustive method.
In addition to increasing the length of the PIN code, the key to solving these security problems is to adopt a more robust encryption algorithm, such as replacing the sequence encryption algorithm with the digital encryption standard DES. DES is a block encryption method, the encryption process is carried out for each data block. In the DES algorithm, the original information is divided into 64-bit fixed-length data blocks, and then the 56-bit encryption key is used to generate 64-bit encrypted information through replacement and combination methods. Unlike the encryption algorithm of the Bluetooth sequence, it can be proved mathematically that the block encryption algorithm is completely safe. The DES block cipher is highly random and non-linear, and the ciphertext and plaintext it generates are related to each bit of the key. The number of available encryption keys for DES is very large, and the keys applied to each plaintext message are randomly generated from this huge number of keys. The DES algorithm has been widely adopted and considered very reliable. Bluetooth technology using DES encryption algorithm can apply Bluetooth to higher security applications, such as electronic financial transactions, ATM, etc.
2.1 DES algorithm
In 1977, the US National Bureau of Standards announced the Federal Data Encryption Standard DES. Because the DES algorithm has strong confidentiality and there is no practical deciphering method so far, DES has been widely used. DES is a block cipher system. It divides the plaintext into groups of 64 bits, and the key length is 56 bits. The basic idea is to use the combination and iteration of transformation to transform each group in the plain text into a cipher text group.
In the DES system, the product transformation is the core of the encryption process,  Perform 16 operations in succession, updating a set of keys each time. The shift transform B is the inverse transform of the shift transform A. Figure 4 shows the encryption process of the DES system. The right side of the figure shows the key generation process of the DES system. The initial key is a 64-bit random sequence. After repeated shift transformation, 16 sets of subkeys (K1 to K16) are generated, and each set of subkeys is used for a product transformation. The so-called initial rearrangement (IP) is to disturb the original arrangement order of the bits in the input packet and rearrange it, and the arrangement mode is fixed.
Perform 16 operations in succession, updating a set of keys each time. The shift transform B is the inverse transform of the shift transform A. Figure 4 shows the encryption process of the DES system. The right side of the figure shows the key generation process of the DES system. The initial key is a 64-bit random sequence. After repeated shift transformation, 16 sets of subkeys (K1 to K16) are generated, and each set of subkeys is used for a product transformation. The so-called initial rearrangement (IP) is to disturb the original arrangement order of the bits in the input packet and rearrange it, and the arrangement mode is fixed.
The operation steps of a product transformation of DES are as follows: (1) The 64-bit input code is divided into left and right groups, each group of 32 bits, represented by Li-1 and Ri-1, respectively. Where i represents the i-th product transformation, i = 1-16. (2) Turn the right group of 32-bit bits of the input packet into the left group of 32-bit bits of the output packet, that is, Li = Ri-1. (3) The 32-bit bits of the right group of the input packet are converted into 48-bit bit code groups through the expansion operation. (4) The 48-bit bits output by the extended transform and the 48-bit bits of the subkey Ki are added in modulo 2, and the 48-bit bits output are divided into 8 groups, each group having 6 bits. (5) Substitute the secret table (S-box) for each group of 6 bits to generate 4 bits. The first 1 and 6 of the 6-bit input determines the number of rows to be selected in the secret table, and the remaining 4 bits determine the number of columns in the secret table. (6) Combine the 8 sets of secret table outputs into 32-bit bits, and then add it to the left group Ci-1 of the product transform input this time by bit modulo 2 to get the right 32-bit output Ri of the i-th product transform.
2.2 Features of DES algorithm
The DES algorithm has the following characteristics:
(1) The secrecy of DES only depends on the secrecy of the key, and the algorithm is public.
(2) At the current level, it is impossible to decipher (that is, parse out the key K or plain text) within a certain period of time without knowing the key. At least a table of 2 56 or 2 64 items must be established. This is Unavailable with existing resources.
(3) Due to the "avalanche effect", it cannot be broken apart, and a change in one bit will cause several bits to change simultaneously.
In summary, the Bluetooth security mechanism built by the DES algorithm is reliable, and it is unrealistic to use exhaustive attack. Suppose a machine that completes DES encryption once per second takes nearly 1,000 years to decipher this password.
The above algorithm can maintain the consistency of the parameters required by the Bluetooth standard in the process of data encryption. It is at the same level as the unit key generated by the Bluetooth algorithm in time, and meets the requirements of the Bluetooth specification.
This article first focuses on the mechanism of Bluetooth information security, and describes the algorithms and implementation steps of each part in detail. Then made a certain assessment of the security of the existing Bluetooth specification, and proposed a new security scheme based on the DES algorithm, which can provide Bluetooth with an improved security design reference for applications with higher security requirements.
Xinxiang Mina Import & Export Co., Ltd. , https://www.mina-motor.cn
![<?echo $_SERVER['SERVER_NAME'];?>](/template/twentyseventeen/skin/images/header.jpg)